AWS Security groups and Network ACLs in AWS can be very discombobulating. If you are planning to take the solution architect exam the chances of getting a question about the difference between these two is very high. In this blog post, you will find out the comparison between these two and when should you use one.
| Security Group | Network ACL | ||||||||||||||||||
| Supports Allow rules only by default all rules are denied }
You cannot deny a certain IP address from establishing a connection |
Supports Allow and Deny rules
By Deny rules we mean, you could explicitly deny a certain IP address to establish a connection example: Block IP address 192.168.0.2 from establishing a connection to an EC2 Instance |
||||||||||||||||||
| Stateful:This means any changes applied to an incoming rule will be automatically applied to the outgoing rule.
Example: If you allow an incoming port 80, the outgoing port 80 will be automatically opened. |
Stateless: This means any changes applied to an incoming rule will not be applied to the outgoing rule.
Example: If you allow an incoming port 80, you would also need to apply the rule for outgoing traffic. |
||||||||||||||||||
| Security groups are tied to an instance. | Network ACL are tied to the subnet. This means any instances within the subnet group gets the rule applied. f you have many instances, managing the firewalls using Network ACL can be very useful. Otherwise, with Security group, you have to manually assign a security group to the instances. | ||||||||||||||||||
| All rules in a security group are applied? | Rules are appliedin their order (the rule with the lower number gets processed first)
Example:
|
||||||||||||||||||
| First Layer of Defence | Second Layer of the defence | ||||||||||||||||||
| Is the Firewall of EC2 Instances | Is the Firewall of the Subnet | ||||||||||||||||||
| Security groups are used for many cases, for example restricting inbound traffic of an EC2 instance to be from Load balancer only. | The same thing applies for Network ACL |
If you are running a production server it is recommended to use a Network ACL. Any EC2 instances launched in the given subnet that has a Network ACL attached has all the Network ACL rules automatically applied. When a VPC is created it comes with a default Network ACL which has all inbound and outbound rules allowed. However, if you create a custom Network ACL both Inbound and Outbound rules are denied. It is a great practice to have SSH restrictions in Network ACLs and in SGs as-well. This scenario makes the ACL act as a backup.
Sample exam questions could be:
- What is the difference between stateful and stateless?
- There are 12 EC2 instances, should you assign a Security Group to each or place them in a VPC and create a Network ACL?
- In a Network ACL, how would deny IP address 95.15.141.101 from Port 80 and Allow other connections?
Security Groups and Network ACLs are part of the security section in the VPC section. It is very important to know the differences and when you should use either.
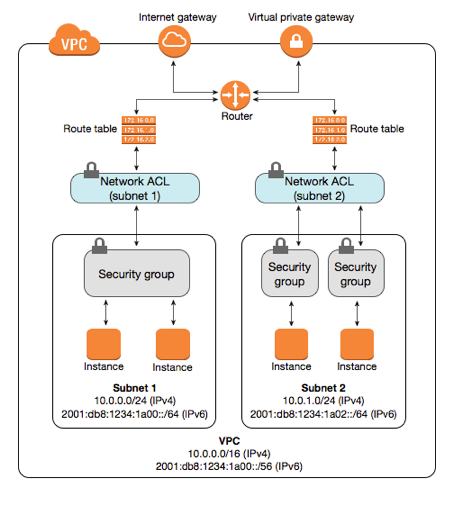
The below diagram displays two Network ACL and four security group. By having a Network ACL and Security group in place two layers of defences have been incorporated. This security strategy is called Defence in depth where several layers of security are placed. In case – if one fails the remaining can protect. Designing a secure architecture is extremely important and it is always best to read some of the latest AWS security white papers or other cloud providers white papers.
As you make changes more frequent within these days, it would be good to use AWS Config to monitor the rules in SGs and ACL. AWS Config monitors the rules and in case if it finds something suspicious for example Port 22 is open to public it will notify you and can also remove the CIDR block.
